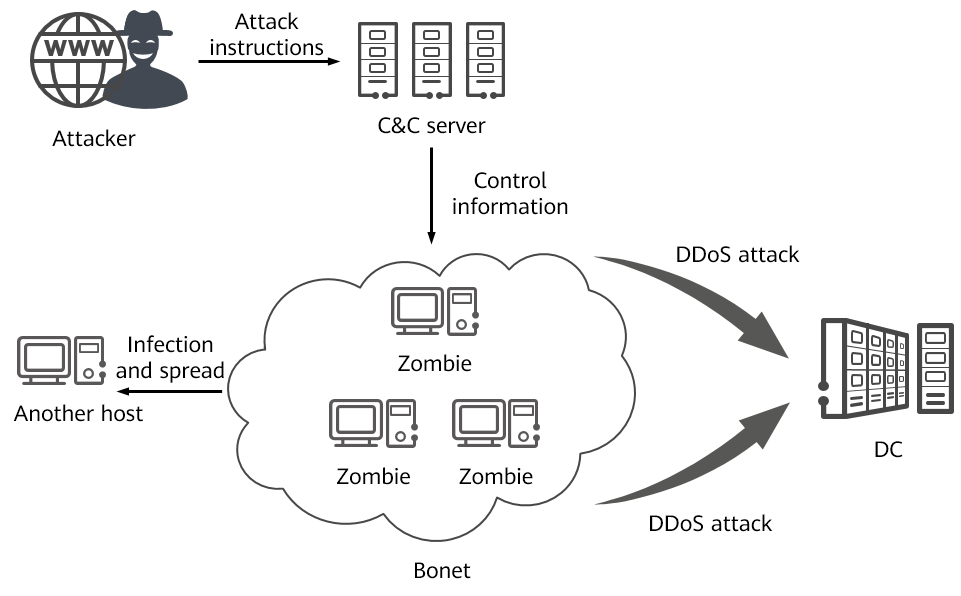
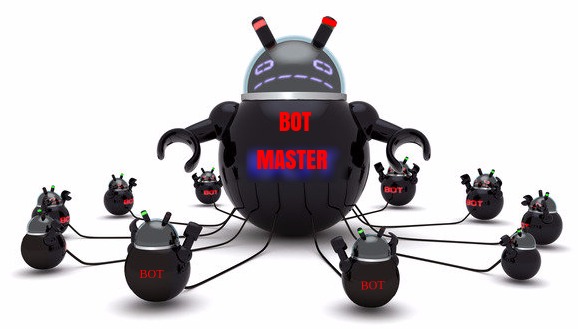
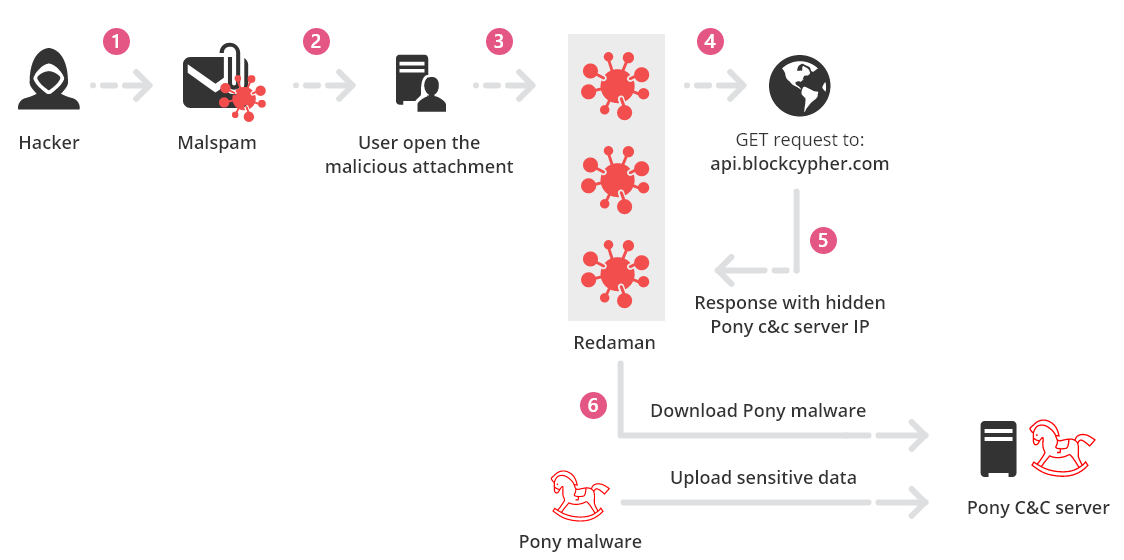
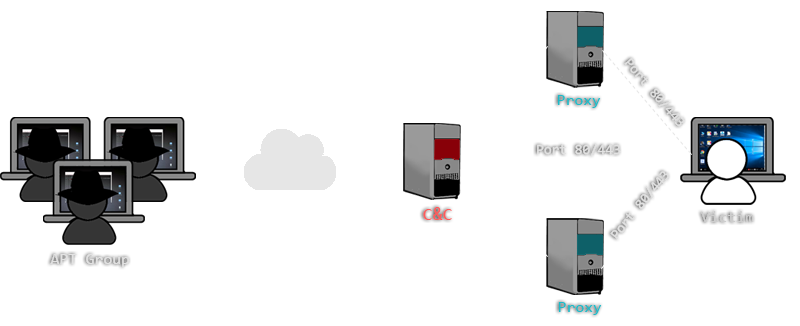
Basic entities of botnet: bots, command and control (C&C) server, and... | Download Scientific Diagram

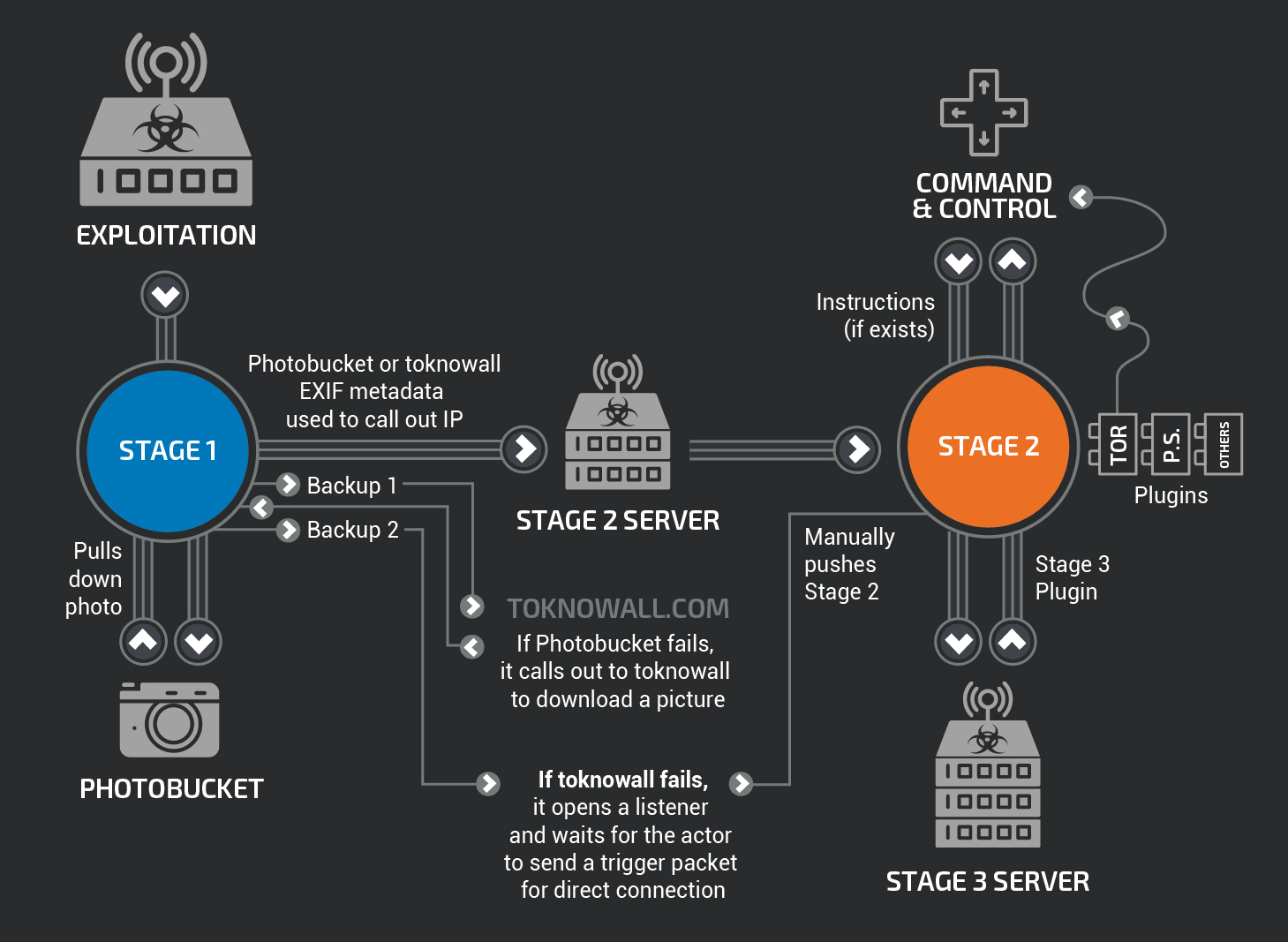
Most Dangerous IoT Malware Mirai Now Using C&C Server in the Tor Network For Anonymity - GBHackers On Security

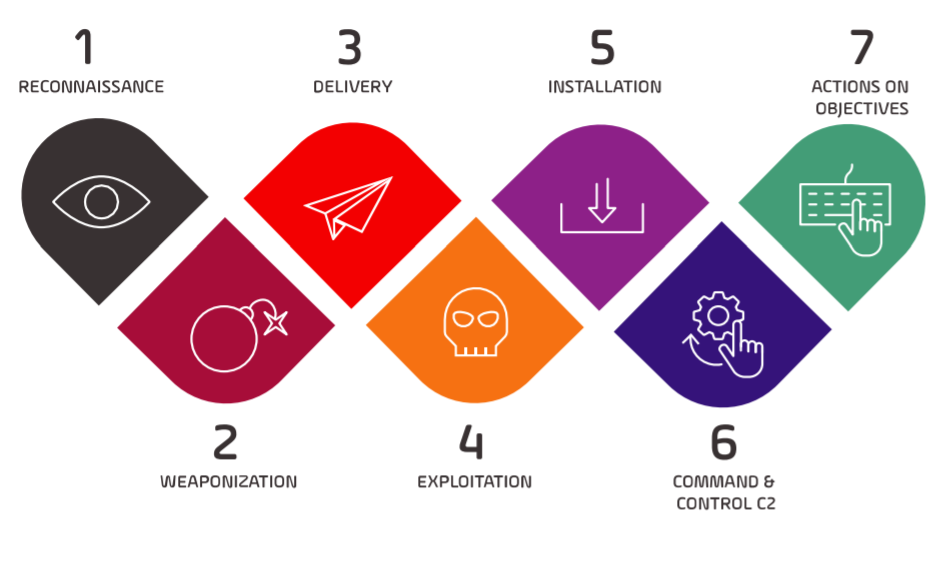
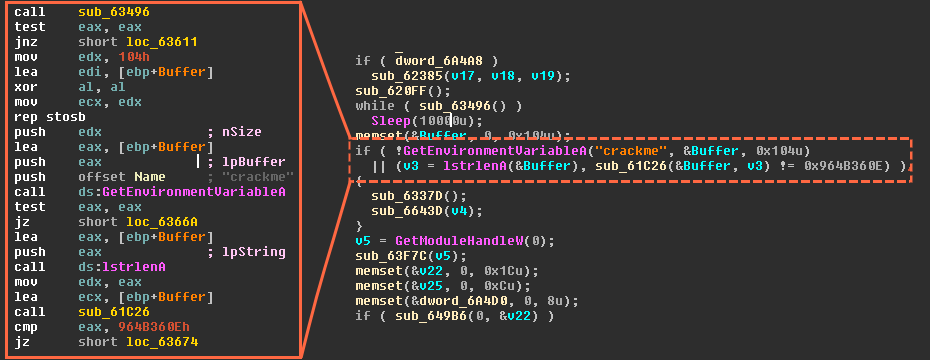
Obtain C&C Channel. Command and Control is a key role to… | by Mohans | Redteam & Blueteam Series | Medium